Review of the Audit Log Is an Example of Which of the Following Types of Security Control
You might be asking yourself, what is an audit log and how do I apply it? Understanding how a log audit operates and why an admin might want to inspect their logs is crucial to business success. In fact, effective audit log management supports compliance, accountability, and security.
Audit log management often goes overlooked in favor of more urgent concerns. However, this guide will explicate why putting audit log direction on the backburner is a mistake. This guide explains what log audits are, their importance, and how y'all can brand the virtually of them. I'll besides suggest log auditing software suitable for business utilise and amid the all-time on the market today.
What Is an Audit Log?
Advantages of an Audit Log
How to Acquit a Log Audit
Best Log Auditing Software
What Is an Audit Log?
An audit log, besides called an audit trail, is essentially a tape of events and changes. Information technology devices across your network create logs based on events. Inspect logs are records of these result logs, typically regarding a sequence of activities or a specific action. Audit logs don't always operate in the same mode. In fact, they vary significantly betwixt devices, applications, and operating systems. But typically, they capture events by recording who performed an activity, what activity was performed, and how the system responded.
Audit logs take notation of just almost every change inside a system, providing a complete runway record of your system'south operations. Therefore, audit logs are a valuable resources for admins and auditors who want to examine suspicious activity on a network or diagnose and troubleshoot issues. These inspect logs can give an administrator invaluable insight into what behavior is normal and what behavior isn't. A log file upshot, for example, will show what activity was attempted and whether it succeeded. This can be useful when identifying whether a system component is misconfigured or likely to fail.
Audit trails can either be manual or electronic records, although the term typically refers to digital records. A log audit could be as simple as a basic file or database tabular array, but it needs some construction to avert becoming confusing. Some people may utilize an audit log review template, which will requite you a tried and tested structure and format. This means you but have to input your logs. If you call up an inspect log review template might exist suitable for you, there are audit log examples attainable online, or they should be embedded inside your auditing software.
One trouble with audit logs is they're vulnerable. If a log audit is misconfigured, corrupted, or compromised in some style, information technology becomes useless, then understanding the basics of audit logging is very important. The near basic forms of audit log management and result log auditing—like manually combing through your records, device past device—are just suitable for small-calibration enterprises. If you desire something scalable, robust, and less prone to homo fault, then log auditing software is a necessity.
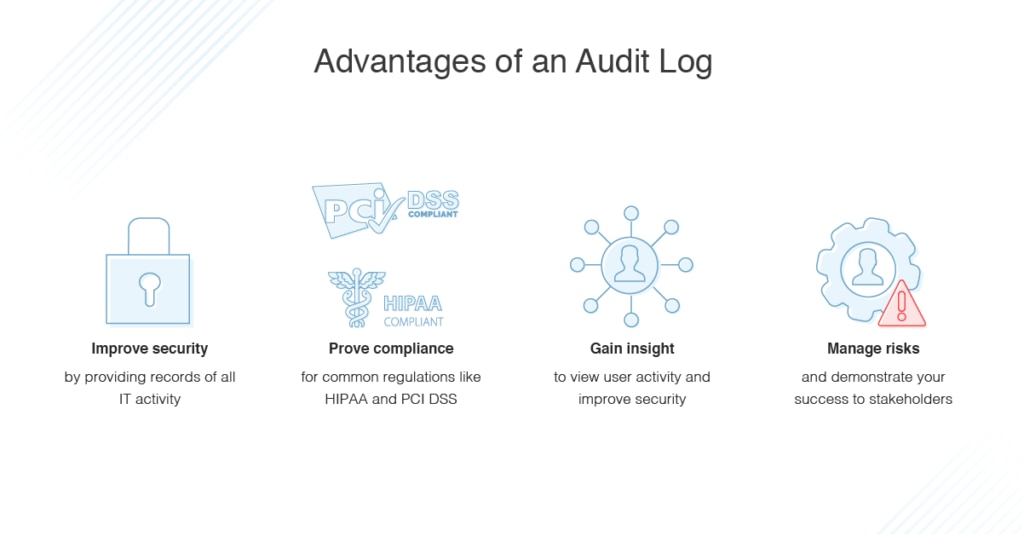
Advantages of an Audit Log
Audit logs offer benefits and advantages for both IT teams and businesses.
Improving Security
Audit logs help with security because they provide records of all It activity, including suspicious action. Inspect logs can help with monitoring data and systems for any possible security breaches or vulnerabilities, and with rooting out internal data misuse. Audit logs tin can even be used to certify document protocols are being complied with and for tracking down fraudulent activeness.
Event log auditing is also important for cybersecurity because it provides records that can serve as evidence. A comprehensive and in-depth log audit tin can make all the divergence in the event of a legal battle and can protect your business concern from liability.
Proving Compliance
Externally, inspect logs are critical for proving compliance with mutual regulations like HIPAA and PCI DSS . Audit logs serve as an official record businesses can apply to prove they were in compliance with the police force. For many businesses, information technology's necessary to share logs with auditors on a regular basis, specially if an result occurs. Using audit logs to comply with regulations can protect businesses from major fines and penalties.
Gaining Insight
Network engineers, help desk staff, developers, and administrators are probable to utilise log audits internally to boost performance, increase accountability, and keep the system stable. Log files provide historical visibility into action, so changes won't go overlooked.
Audit logs record how often someone accesses a sure document or file, which can give a company invaluable insight. You can use a log inspect to learn about user activity, which could be used to heave efficiency, security, and performance.
Hazard Direction
Having a robust risk direction strategy is of import for any business organization. Inspect logs play a key part in risk management considering they permit you show partners, customers, and regulators you're taking measures to prevent issues before they occur. This could show an investor you pose a reliable and depression-risk investment opportunity.
How To Conduct a Log Audit
Showtime and foremost, you lot should understand what fields to audit when an upshot occurs. The information included in the log should provide the context of the upshot, the "who, what, where, and when," and anything else of relevance. The post-obit fields are critically of import:
- Group (i.east., the squad, organization, department, or account from which the activity originated)
- Histrion (i.e., the uuid, username, or API token name of the account responsible for the action)
- Effect proper noun (i.east., the standard name for the specific event)
- Clarification (i.east., human-readable, may include links to other application pages)
- When (i.e., the server NTP synced timestamp)
- Where (i.east., the country of origin, device identification number, or IP address)
- Activity (i.east., how the object has been contradistinct)
- Activity Blazon (i.e., create, read, update, or delete)
Y'all might also include the server ID or name, server location, the version of the code sending the event, the protocols (i.e., https or http), and the global actor ID.
Before deciding what degree of auditing is necessary, you should conduct a chance assessment for each organisation or application. At the very least, all the same, you'll have to log the following: user IDs, engagement and fourth dimension of logging in and logging off, failed and successful access attempts, terminal identity, networks accessed, files accessed, system configuration alterations, system utility usage, security-related events, exceptions, network connection changes or failures, attempts to alter security settings, and the activation of protection systems like anti-malware. These components contribute to admission control monitoring, allowing you to investigate audit trails if there'due south an incident.
Making certain you sync the timestamp is another key chemical element of log inspect management. Without the logs timestamp field using a common format, it would be practically impossible to acquit sequential analysis. NTP, time protocol, should be synchronized for all servers, devices, and applications, as this is a compliance requirement for numerous standards.
Log file security is as well important. Log audits are prime number targets for anyone intent on hiding show of their activeness or wanting to compromise and corrupt data. To prevent this from happening, information technology's best practice to configure audit logs then strong access control restrictions are established for the logs. This usually includes limiting the number of users who can alter log files. It is too best practise for all transmissions of audit logs to be encrypted.
Best Log Auditing Software
Log audits are a difficult business organization. Though they're important for several reasons, a lot goes into maintaining them, and manually managing your ain logs can be both a time-consuming and error-prone process. If yous want to free up fourth dimension and make your log auditing operations more than efficient, and then SolarWinds® Log Analyzer, SolarWinds Security Effect Director, and SolarWinds Access Rights Managing director are the all-time tools money can buy.
All three of these tools boast convenient, dynamic dashboards that display data in a graphical, easy-to-interpret manner. Security Event Manager automatically monitors your application security audit logs, detecting issues in real time. Abnormalities are flagged, and the program gives you relevant security recommendations. It analyzes server log information and provides color-coded results, helping you prioritize the almost important elements.
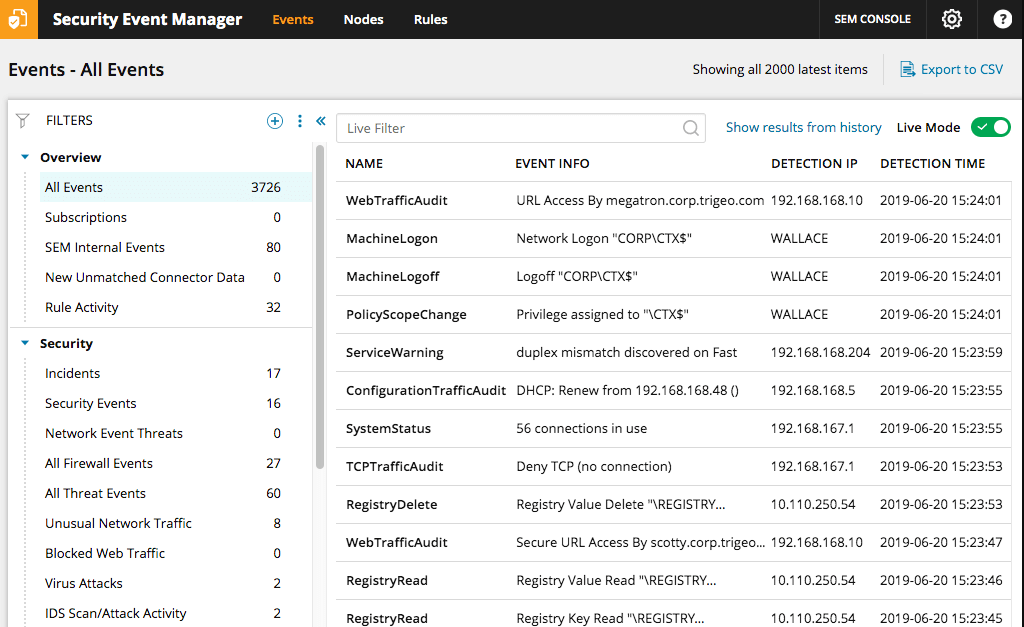
Security Event Manager also helps streamline account command and forbid privilege abuse, alerting you lot whenever to unusual logins or information modification. The programme can decommission any suspicious accounts and lets you reassign security groups quickly and easily. This software is also great for demonstrating compliance, because information technology lets you generate security reports specifically designed to show compliance with GLBA, SOX, NERC, HIPAA, and more than. A free trial of Security Event Manager is available.
Log Analyzer, a log management and analysis program past SolarWinds, takes a more functioning-based rather than security-focused arroyo to log audits. This tool allows you lot to perform log data analysis on server and network devices. You're afforded fundamental insight into a range of information types, including SNMP traps, syslogs, and Windows issue logs. With all this near real-time critical log data collection, centralizing, and analysis, your troubleshooting can be more than accurate and happen more chop-chop.
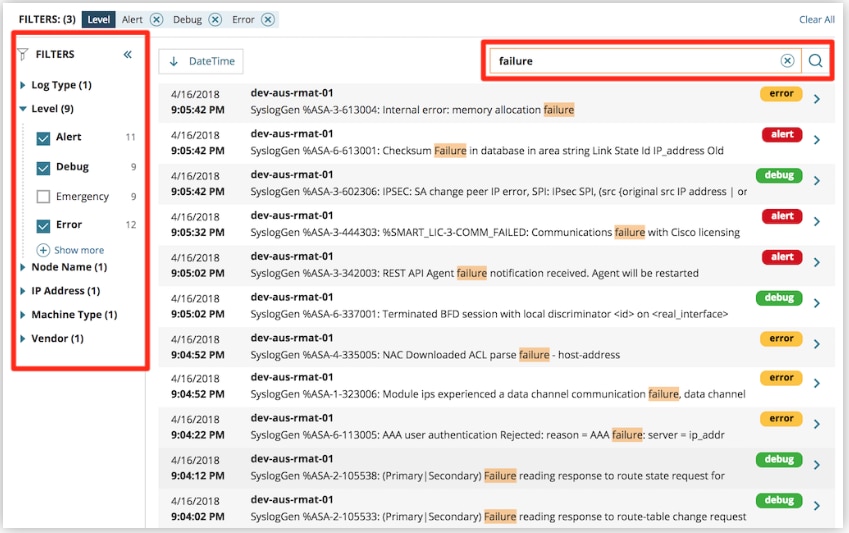
Another do good of Log Analyzer is information technology lets you lot filter your log information via an intuitive, built-in search engine. You can refine your search with out-of-the-box filters like log blazon, node proper name, machine type, vendor, and more than. Searching your logs couldn't be easier.
1 of the best Log Analyzer features is its information visualization features, including interactive charts. This assists with rapid and accurate analysis, in addition to unifying infrastructure performance. A free trial of Log Analyzer is besides available.
If you're looking for a tool focused on access rights, you need SolarWinds Access Rights Manager. This tool offers ongoing visibility into the access rights of everyone on the network. Compliance requirements need granular and comprehensive insight into user access rights, and with ARM , yous tin easily cheque who has access to critical and sensitive data. What's more, if suspicious changes or action have identify, ARM instantly sends an alert.
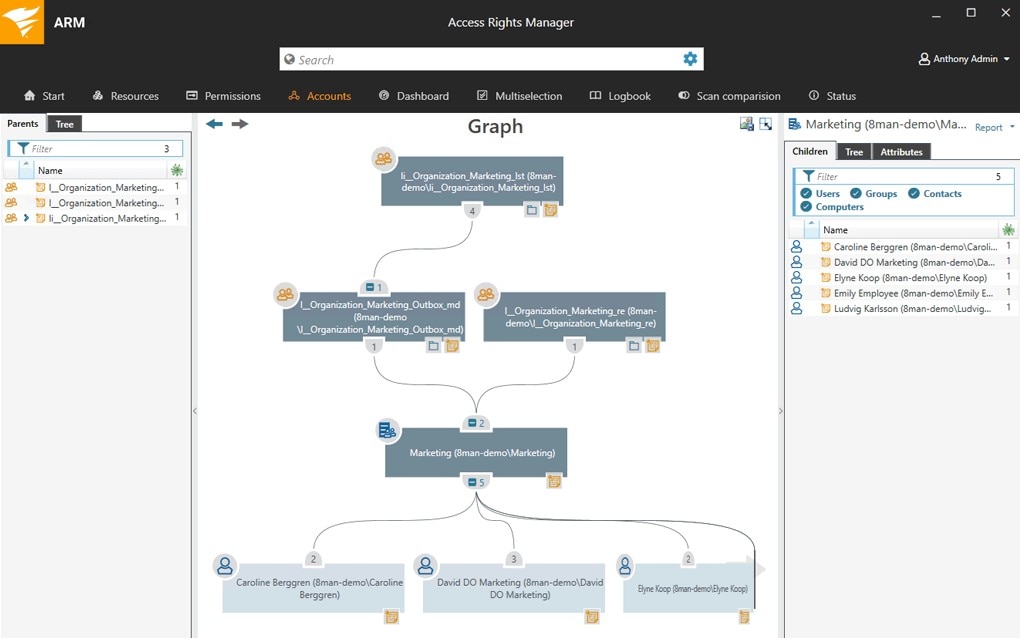
In terms of audit logs, it'southward easy to use ARM to generate the custom reports you need—you lot can use audit reports to rails user provisioning and beliefs internally, while for auditors, you tin evidence you lot've handled access rights co-ordinate to compliance regulations. Endeavour ARM free for 30 days.
quinlivanlicninhat.blogspot.com
Source: https://www.dnsstuff.com/what-is-audit-log
0 Response to "Review of the Audit Log Is an Example of Which of the Following Types of Security Control"
Post a Comment